Cybersecurity & Forensics Training

Security Information and Event Management (SIEM) is software that improves security awareness of an IT environment by combining security information management (SIM) and security event management (SEM). SIEM solutions enhance threat detection, compliance, and security incident management through the gathering and analysis of real-time and historical security event data and sources.
Business Planning & Strategy
SIEM has a range of capabilities that, when combined and integrated, offer comprehensive protection for organizations. A SIEM supports the incident response capabilities of a Security Operations Center (SOC), which includes threat detection, investigation, threat hunting, and response and remediation activities. This is also made easier and more efficient by being brought together into one dashboard. SIEM provides enterprise security by offering enterprise visibility.
Contacts
Visit Us Daily
Corporate Office
Have Any Questions?
+880 9614501126
How It Works & How We Do It

Your Imagination Is Our Creation
It’s a daunting challenge: How do you move forward at speed despite enormous uncertainty? Radar Strategy provides the answer. Our unique “Today Forward, Future Back” approach enables you to create value now as you move toward your future vision, with the flexibility to adapt as scenarios change. We’ll help you make critical choices and choreograph your transformation journey as you bring your core to full potential and build new growth engines.
Our team of global experts help you achieve sustainable, organic growth by focusing on three critical building blocks: an outside-in approach that puts customers first, a uniquely great customer experience and internal capabilities that ensure you deliver optimal customer interactions at every touchpoint.
marketing analysis
business innovation
finance strategy
We are Always Ready to Assist Our Clients
Developing Technical processes and procedures
How It Works & How We Do It
Our specialists are ready to provide an analysis of both the market as a whole and its individual components (competitors, consumers, product, etc.), using practical methods and starting from your research goals.
- the organization is just beginning to operate in the market, implementing some projects. Our team of global experts help you achieve sustainable, organic growth by focusing on three critical building blocks.
- there are projects that require temporary expansion of the marketing department. Customer-focused businesses build a virtuous cycle we call the "customer wheel." We help you at every stage of growth, developing custom solutions and collaborating with all levels of your organization.
- there are projects that require temporary expansion of the marketing department. Align your marketing and brand strategy with overarching business objectives. We help you combine hard metrics with creative.
It allows you to effectively
FREE TRAINING FOR LAW ENFORCEMENT
Business Planning & Strategy

Nurture promoters, your loyal customers who are more profitable and will advocate for your business—both in good times and bad.
Customer-focused businesses build a virtuous cycle we call the “customer wheel.” We help you at every stage of growth, developing custom solutions and collaborating with all levels of your organization. Identify quick, targeted customized solutions and operational improvements.
Cyber Security Services
- Attack Surface Assessment
- Anti Theft Security
- Active Cyber Defence
- Artificial Intelligence
- Bank Vault Security
- Brute force attack
- Cyber Attack & Strategy
- Cryptography
- Dictionary attack
- Ethical Hacking
- Email Security
- External Vulnerability Assessment
- Facebook Security
- Firewall Security
- Face Recognition Security System
- Hashing algorithm with rainbow Table
- Hacked Website Repair
- Malware Scanner
- Network Security
- Patching
- Penetration Testing
- Phishing
- Server Security
- TCP-UDP Port Scan
- Website Security with Scan
Contacts
Visit Us Daily
Corporate Office
Have Any Questions?
+880 171675 6661
Mail Us
Video Forensic Software
Recovering CCTV footage is a relatively simple task, depending on how quickly you act and how old the surveillance video was. Nonetheless, it’s crucial to know how to recover overwritten CCTV footage safely and quickly because of how important it is for enterprises and home users alike. In the sections below, we’ll take you through the overwritten CCTV file recovery process, as well as the factors that affect the success rate of the process.
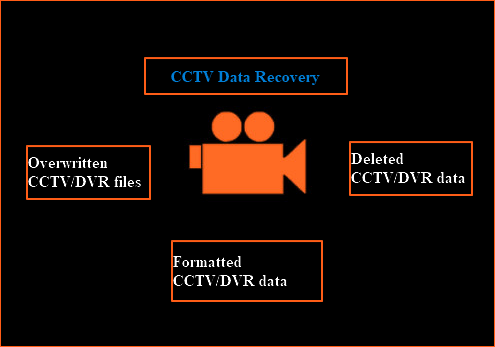
Disk Extraction: bypassing the DVR passwords enables forensically extraction of videos in normal conditions, furthermore recovers the Lost, Deleted, Overwritten, and Fragmented files. Network Extraction: supports video recovery from the surveillance host or router through a remote network download module. Automatically detects the surveillance host IP and configures local host IP, after the network is connected, VIP can export large volumes of data as quickly as possible.
RETRIEVE OVERWRITTEN CCTV FOOTAGE ?
Recovering Deleted DVR Video with DVR Examiner
Conclusion: Although various forms of surveillance are much more common and easier to deploy than ever before, the quality of the recorded footage can be influenced by environmental factors such as visibility, distance, the motion of travel, and others. But thanks to modern forensic video enhancement techniques, although no silver bullet, the quality of the footage can be improved for better clarity without compromising the integrity of the evidence.
Services
- Recover CCTV/DVR/NVR Files
- 3rd Party Cloud Software
- Linux Base Clint Monitor
- Point to Multi-point Transmission
- support functions
- Network Design & Planning
Contacts
Visit Us Daily
Sino Atrium
Have Any Questions?
+880 1716756661
Mail Us

What Is Digital Forensics and Incident Response (DFIR)? Digital forensics and incident response are branches of cybersecurity that involve identifying, investigating, containing, remediating and potentially testifying related to cyberattacks, litigations or other digital investigations.
DFIR provides a deep understanding of cybersecurity incidents through a comprehensive forensic process. DFIR experts gather and investigate vast amounts of data to fill in gaps of information about cyber attacks, such as who were the attackers, how they broke in, and the exact steps they took to place systems at risk. In the event of a successful breach, DFIR can also help identify the data lost or exact damage caused [expand title=”Read More” swaptitle=”Read Less”]DFIR capabilities typically include: Forensic collection gathering, examining, and analyzing data from networks, applications, data stores, and endpoints, both on-premises and in the cloud. Triage and investigation—determining whether the organization has been breached and identifying the root cause, scope, timeline, and impact of the incident. Notification and reporting—depending on the organization’s compliance obligations, there may be a need to notify and report on breaches to compliance bodies. In addition, depending on the severity of the incident, there may be a need to notify authorities like the FBI and Cybersecurity and Infrastructure Security Agency (CISA) in the US. Incident follow up—depending on the nature of the incident, there may be a need to negotiate with attackers, communicate incident status to stakeholders, customers, and the press, and make changes to systems and processes to address vulnerabilities.[/expand]
- Security orchestration, automation, and response (SOAR) technologies can autonomously identify security incidents and respond to them. SOAR solutions leverage machine learning to analyze security events, and can automate complex security processes to respond to them. To this end, they integrate with other security tools such as firewalls and endpoint security.
- Scope of service—DFIR services can be proactive or reactive. Proactive services include activities like threat hunting, vulnerability testing and security education. Reactive services include incident response and attack investigation.

After a security breach or compromise, incident response services are used to manage the incident in real time. Incident response refers to the actions taken immediately following an attack to contain the incident and preserve all evidence for later analysis. A successful incident response requires a team of experts who can handle complex breach events quickly and precisely while preserving the evidence.
Services
- digital forensics and incident response (dfir)
- Organizational Audit
- business consulting
- project management
- support functions
- finance planning
Contacts
Visit Us Daily
Sino Atrium
Have Any Questions?
+880 1613488930
Mail Us
Everybody engaged or involved with First Response Training is a specialist in their own field, having gained that knowledge and experience through a law enforcement, military, intelligence or specialist career.
First Response only provide training courses that are written or delivered by the best practitioners available. Our trainers are active operators who also teach, which ensures that our courses are always up-to-date, reflecting not just changes in technology, but industry best practice and compliance with laws and regulations across the various jurisdictions we operate in. We offer a catalogue of specialist training courses and the ability to deliver ‘ad-hoc’ packages to suit your particular requirements.
The NSRiC (Canada) was developed to enhance the awareness, expand the education, and build the capacity of justice and public safety agencies to prevent, investigate, prosecute, and respond to cyber threats and cyber crimes. It is intended to be a national resource for law enforcement and related justice and public safety entities.
The NSRiC addresses three principal functional areas:
- Cyber crime investigations
- Digital forensics
- Information systems security
DF SOLUTION
- Digital Crime Scene Equipment
- CCTV/ Video Forensic Equipment
- Mobile Enterprise Triage
- Mobile Triage Equipment
- Digital Triage Equipment
- Network Security Forensic Equipment
- Miscellaneous Forensics Equipment
Contacts
Visit Us Daily
Sino Atrium
Have Any Questions?
+880 1716756661


